CSG3309 IT Security Management Assignment Presentation
Assignment Detail:-
- Number of Words: 3000
Learning Outcomes
The purpose of this assignment is to support the following unit Learning Outcomes (LO) for this unit.
- Outline the impact of ethical issues, and compliance on information technology security management
- Collaboratively analyse and report on information technology security management issues and emergent
- Propose a solution for information technology security management issues
Purpose
John Dough is undertaking a security improvement programme. The programme aims to reduce information security risks to John Dough by implementing a range of security measures.
The work is to be undertaken by a 3rd party “IT Security Management Company” but the decision has not yet been made as to which company is best suited to do the work. As such, a “Request for Quote” is being sent to three large security firms.
The deliverables are separated into two parts.
Part 1:
You are to act as a technical security consultant who has been hired to develop a specification of scope and requirements that will be sent to other (larger) security consultancy firms so that they can provide a quote to John Dough pizza.
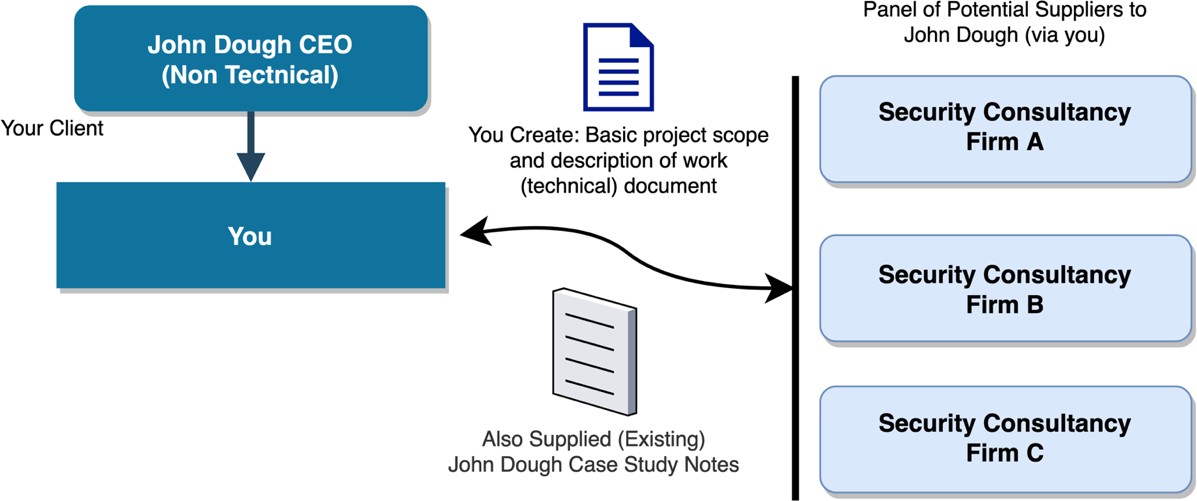
Your job is to help develop and describe the IT security requirements to be included in the request for quote. To do this, you must narrow down the goals of the security improvement programme and develop a basic scope that satisfies the programme requirements of John Dough Pizza.
Your scope and programme requirements document will be sent (along with the original John Dough case study documents) to three security firms. They will use your document to create their proposals and present these proposals (and cost estimates) back to you and your client, John DOUGH Information Security Proposal (Remediation and Management).
You need to be clear in the IT Security requirements for John Dough. You must communicate the requirements, rationale and goals to the external contractors, so they understand what your client needs.
You need to justify to your client John Dough how you arrived at your decisions and how your scope will help them get the best “bang for buck” on their information security investment.
Task: Create a basic proposal (initial project scope, description of work and requirements)
Submit: 5-6 pages maximum (including all attachments, and appendices. Not including cover pages, table of contents or references).
Content:
You are to present a document that details what remediation and ongoing work should be done for John Dough. You must base this on your analysis of John Dough’s information security situation.
The document should be able to be read by security professionals so that they can understand exactly what services and work they must provide to John Dough.
You do NOT need to write the entire proposal. Your job is to make clear what John Dough requires and why.
Part 2:
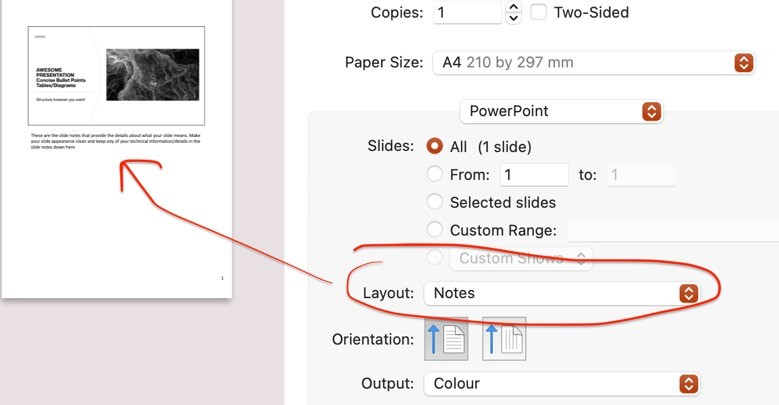
Task: Create a presentation (PowerPoint presentation – max 6 slides with detailed notes)
Submit: 6-page maximum PowerPoint Presentation BUT this must be printed to PDF so that it contains the slides AND the detailed speaker’s notes (you will submit only the PDF). The purpose of this document is to provide a summary and rationale for your proposal in language that John DOUGH can understand and rationalise.
Content:
The presentation is a non-technical summary and rationale. You will give to YOUR client (John Dough) to explain what you did, why and what it will achieve once you have awarded the contract to a security firm. This is to help them understand the proposal document you’ve created and prove that you will have improved their overall information security position.
Specific Requirements and Assessment
Your document and presentation must show that you have a good understanding of:
- The threat landscape in the context of a pizza business
- Provide a threat map (categorised using the 12 threat categories) that is easy to understand for John DOUGH. This could provide the justification (the WHY) part of your
- How to apply classic goals of cyber security in analysis of security
- Discuss and analyse confidentiality, integrity and availability compromises that have, or may occur in the
- Assess potential legal, ethical or cultural issues
- Identify any legal, ethical or cultural issues that need to be addressed in the IT Security programme
- Consider legalities that may arise due to insecure systems
- Consider legal, ethical, or cultural issues that may occur from having a 3rd party undertake the security
- Identify the root cause of security incidents described in the case study document
- Develop an explanation as to why. This does not need to be exhaustive, moreover a brief summary of what occurred and why. You should address the impact on the Confidentiality Integrity and Availability of information in your discussion and/or future impact.
- Governance, Strategy and Policy as part of your assessment
- Show that you have considered how the IT Security Programme being proposed relates to aspects of governance, strategy, and
The above points can be addressed in either document, but you must demonstrate your ability to analyse a given case study and communicate information security issues professionally regardless of your audience.
Are you looking for a CSG3309 IT Security Management Case Study Assignment? We are providing you with Management Assignment Help at a nominal rate. Assignmenttask.com delivers quality written work with 100% plagiarism free content. You can avail yourself of our Free Assignment Answers by experts at anytime and anywhere.
For REF… Use: #getanswers2001964

