CSG3309 Information Security Management Assignment Help
Assignment 2: Group Case Study: John DOUGH Pizza
Learning Outcomes
- The purpose of this assignment is to support the following Unit Learning Outcomes (LO) for this unit.
- Collaboratively analyse and report on information technology security management issues and emergent trends.
- Propose a solution for information technology security management issues
Background
John Dough is undertaking a security improvement programme. The programme aims to reduce information security risks to John Dough by implementing a range of security measures.
This assignment continues from Assignment 1. For Assignment 2, you will switch roles from a technical consultant to an information security team responding to your own proposal/scope document.
You will assume the role of one of the security companies mentioned in Assignment 1.
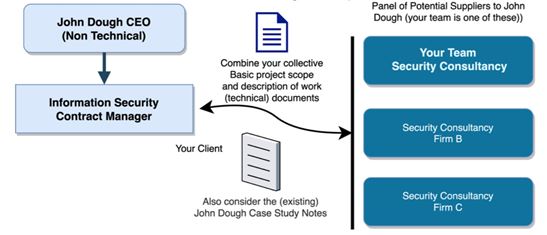
Your job is to provide a response to the proposal document and explain how your company will address the requirements of John Dough pizza. Note that you are in competition with other security firms, but you do not compete on price — you compete on your technical skills and demonstrable excellence and knowledge of the information security industry. That means, you need to demonstrate why “Your Team Security Consultancy” has a better understanding of John Dough’s security position and how your firm will offer better security, skills, and value than Firm B and Firm C.
Task: Continue from Assignment 1
Working in a team, you are to share and read each other’s assignment 1 documents for the “Project scope and description of work” documents (created for assignment 1).
You are to consider the best aspects of each of these proposal documents (i.e., combine aspects of each of your assignment 1 documents to come up with the proposal presented to your company). I.e., the proposal/case-study you are responding to is to be a hybrid of all group members’ previously submitted assignment.
- Assign the following roles to teams. Depending on the group size, members may need to take on multiple roles.
Teams:
- Manager of Risk Assessment Team
- Manager of Security Implementation Team
- Manager of Security Policy & Compliance Team
- Manager of Project Management Team
Working as the leaders of your respective teams, you are to prepare a section of the response to the proposal document (which you created based on combining aspects of each other’s Assignment 9 submissions).
You should work iteratively as individuals BUT also as a team. So, for example:
- Initial risk assessment should feed into other teams to show how risk will be reduced if the proposal is successful
- Security implementation teams should consider the documents created by the security policy and project teams to explain how they will roll out parts of the solution
- Security, Policy and Compliance team should consider the risk assessment
The main goal is to have your final presentation — created by 4 different ‘managers’ become one cohesive plan
Specific requirements and Assessment
A. Risk Assessment:
An IT security risk assessment (assets, threats, vulnerabilities). The risk assessment should be prioritised to handle the greatest risks to the business first. This task will require:
- asset identification (Maximum of 30 assets) and;
- a weighted factor analysis (WFA) to prioritize business assets. You need only perform WFA on 15 assets.
- Justification of your WFA criteria and weightings. The criteria must make sense to the business and provide a framework for reasonably assessing the importance of assets.
Note: Consider all components that are involved in IT Security Management (i.e., People, Procedures, Hardware, Software, Data, loT, Network.
Your assets should relate, where possible, to Assignment 1.
You are addressing the request for proposal / scope document, so you need to keep this is mind. If however you find you have missed critical assets in Assignment 1 you will need to address those assets here.
B. Project Management Overview:
Create a Work Breakdown Structure (WBS) to manage the tasks for this project.
Note: This is NOT a project management unit, but there are some similarities. It is important that your client understands what work you propose to do. This means you do not need to apply full project management methods to the problem, but you should describe the overall list of tasks/processes that will help secure your client.
C. Demonstrate understanding of current Industry Standards and Best Practices: Reference the relevant industry standards, benchmarks, whitepapers, or best practices (researched or proposed). For example, if you base your solutions on standards, reference which standards are used (e.g., IS027001/2. NIST publications, CIS Controls, ISM).
D. Policy and Compliance:
Address compliance requirements (if any) at the executive or functional level of the business.
- Are there specific information security laws / policy governing certain technologies?
- Do you need to create any supporting policy?
E. IT Security Programme Implementation:
Describe the proposed implementation strategy, i.e., Direct, Phased, Parallel, Direct Changeover. This section will form part of a work package and can be addressed in the WBS.
F. Operational security:
What security controls would be suitable for the identified risks, list the controls and remediation.
Include in the proposal a contingency plan. This need only be an outline of how you propose to address Business Continuity. For example, what plans you recommend for John DOUGH (IRP, DRP, BCP). The proposal does not need to include these plans, BUT, you do need to demonstrate you understand the importance of, and have thought about contingency planning.
G. Cost/Budget Estimates
A draft budget on how much these changes will cost (rough estimates are fine — BUT you must support your numbers if you use them). This could include estimated:
- staffing costs
- IT technology costs
- training costs
- hardware costs
- insurances
- funding for additional research.
Hint: the WBS will have most of this information
H. Ares for future security programmes, research, and improvement:
There will undoubtedly be security areas of concern that are out of scope for this proposal, attributed to time and financial constraints, Nonetheless, in concluding, provide
a brief overview of future projects that John DOUGH will need to consider moving forward. This can be written or table format and need not be exhaustive.
Future projects will likely include low information security risks derived from the Risk Assessment, or other programs such as Awareness and training.
All your recommendations should be derived from the Risk Assessment.
Are you finding CSG3309 Case Study Assignment Help on John Dough Pizza? We have well-experienced writers who assist you with Information Security Management Assignment Help at a reasonable price. Get subject matter expert assistance with 100% plagiarism free content at Assignment Task. Our service is fast, dedicated and provides quality material.
For REF… Use: #getanswers2002049

